Mobile nowadays has become more front and center in the enterprise landscape. It is both directly and indirectly creating new revenue or strengthening the existing revenue streams. Companies that listen and respond properly to mobile trends can win competitive advantages. Is your organization mobile ready
Mobile nowadays has become more front and center in the enterprise landscape. It is both directly and indirectly creating new revenue or strengthening the existing revenue streams. Companies that listen and respond properly to mobile trends can win competitive advantages. Is your organization mobile ready
Here are five key questions to ask as you prepare for your company to go mobile.
1. Is your business model mobile ready?
It’s apparent that mobile is now everywhere and significantly changing the way businesses operate. It is considered to postdate the days of personal computers and is becoming the main tool of the business workforce. All stakeholders who are influencing your business, including customers, business partners and employees, are also profoundly being influenced by mobile technologies. They are going mobile. New work flows and connection patterns are being created among your business influencers. Customer demands are getting more sophisticated with all the mobile options, which may force your company to reexamine a lot of things, including its business model, to reposition where it is in the value chain. Revenue streams are shifting to where the mobile involvement is, and you have to refine your business model accordingly to keep your customer happy as well as catch new opportunities. Mobile is where the customers are, so that’s where you need to be.
2. Is your infrastructure mobile ready?
A research study from IBM states that 91 percent of mobile users always keep their mobile devices within a reachable distance. It implies that users want the ability to access applications and services everywhere, whenever they are needed and of course as quickly as possible. This challenges your infrastructure in terms of availability, performance and responsiveness to the explosive number of requests.
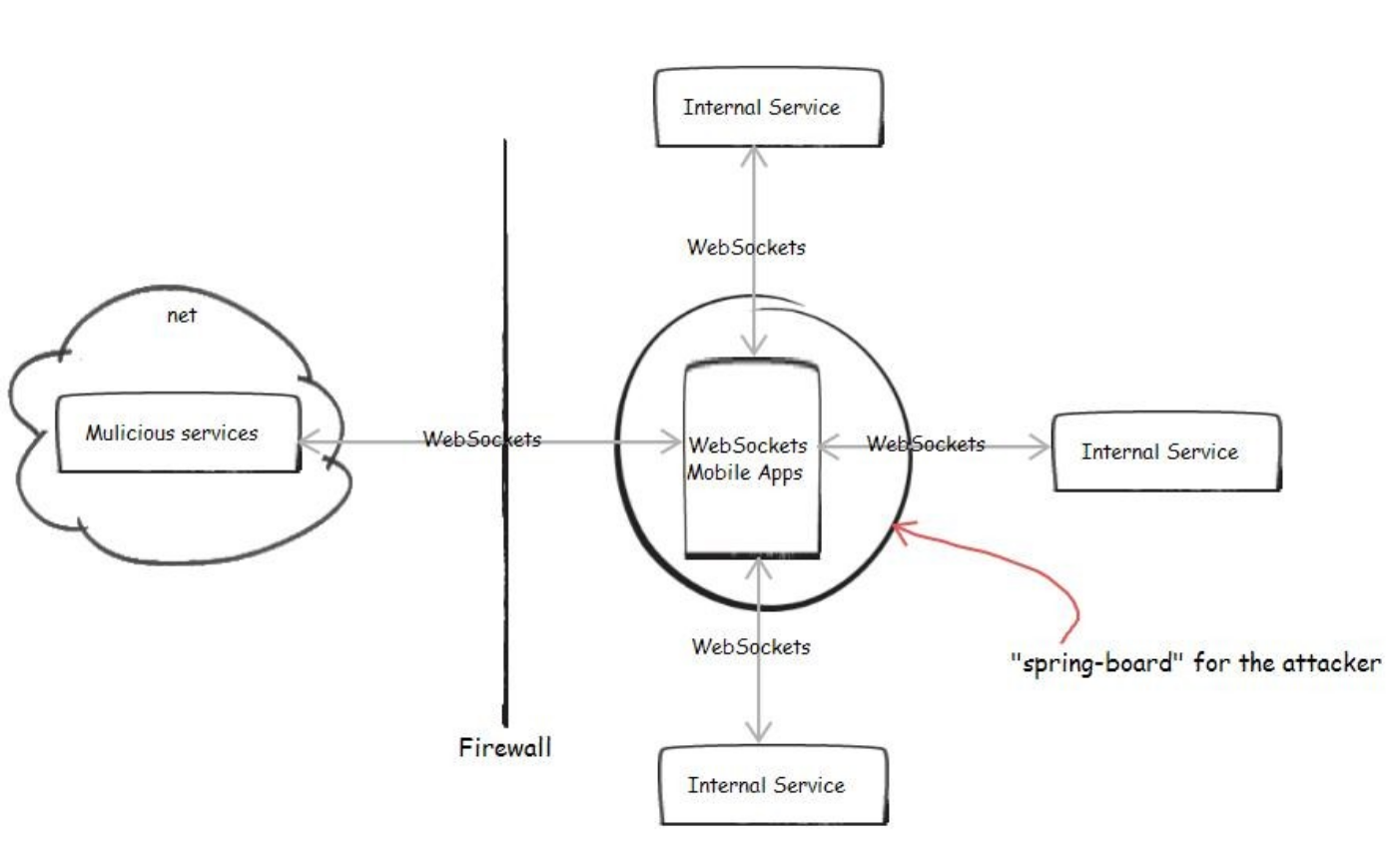
The wide adoption of mobile devices also challenges your current system’s architecture. Technically, services that have been exposed outside of the enterprise might not be suitable for mobile requests because in responding to the requests from a mobile environment, which is typically limited in computing resources, the data being transferred back should be lightweight enough that it can be effectively consumed by mobile applications to provide the expected user experience.
Additionally, the diversity of mobile platforms that involve platform owners in operating some useful services (for example C2DM or APNS, the users’ service providers and so forth) would require your enterprise system to be adapted to interact with those external systems effectively and securely.
3. Have you considered security?
Security has always been a big concern when enabling an enterprise to go mobile. Controlling security for mobile is getting more and more challenging due to the natural portability of the mobile environment as well as the constantly growing diversity of mobile platforms and mobile applications. It consequently requires an efficient approach from the strategic level with clearly defined mobile use cases in the business context. This in turn helps the enterprise to build up a comprehensive mobile security policy to more detailed levels, like how to use technologies for implementing the policy and how to make mobile users aware of security threats and regularly educate them to follow security practices to protect themselves and the corporation. That circle from strategy to policy to technology and education should incrementally, iteratively evolve to keep your security strategy up to date and ensure that it reflects your business needs.
4. Is your design approach and concept mobile adequate?
Mobile devices are typically made with smaller screens and are several times less powerful than desktop computers in terms of computing resources, yet the activities performed on mobile require a sense of immediacy. They tend to be tactical in nature. As a result, the interaction flow between the user and the mobile application requires a completely new user experience design mindset. Data presented on mobile needs to be somehow contextualized and condensed to convey as much information as possible and to best utilize less network bandwidth and hardware resources. There is no room for redundancy. Information and an application’s features need to be progressively, selectively displayed.
Design approaches applied for desktop are consequently inadequate for the mobile environment, not only from the user interface perspective but also from code design since the same code would not run on mobile as effectively as on desktop. It needs to be leaner.
Mobile is becoming mainstream in the workforce, and a mobile application is no longer simply a smaller, zoomed-in version of your desktop application. Applying an appropriate design mindset will make your mobile application, the heart of your mobile business model, more attractive to help you meet user expectations and gain a competitive advantage.
5. Is your application development process mobile suitable?
Mobile devices and platforms evolve rapidly, and your app consequently needs to adapt quickly to those changes in order to continuously gain user satisfaction. In other words, mobile apps are written, used and replaced at a much higher rate than traditional enterprise apps. That requires your development process to be refined so that your app will be iteratively delivered more quickly without sacrificing quality.
Additionally, mobile user expectations are very high, yet loyalty is low. They will easily forget your app if they cannot find what they need on the very first try on their tiny mobile devices. In order to continuously make sure your app satisfies its users and keeps them using the apps, you need to get them involved in the development of the apps earlier, interact with them more frequently to get feedback and then meet their expectations promptly—period.